I run the latest Wordpress on Plesk. I got an alert through WP Toolkit today that a high priority vulnerability has been identified by Patchstack:
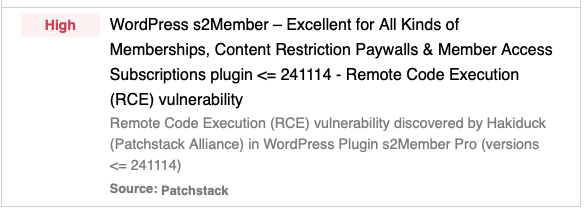
Are the developers aware of this vulnerability and when can we expect to receive a patch?
Thanks.

I run the latest Wordpress on Plesk. I got an alert through WP Toolkit today that a high priority vulnerability has been identified by Patchstack:

Are the developers aware of this vulnerability and when can we expect to receive a patch?
Thanks.
Any more details on the vulnerability?
We’re seeing this too, on the SolidWP Security Report: https://solidwp.com/blog/wordpress-vulnerability-report-december-4-2024/
Patchstack - “This vulnerability is highly dangerous and expected to become mass exploited.”
I have a Pro account, so I have just tried contacting @clavaque directly, using the “s2Member Pro Question? Contact Us” button on: https://s2member.com/support/
In another thread, he says he “checks the support inbox daily”: Pro member support not responding
Hopefully we will get more details soon.
It may be that the vulnerability is only an issue under specific, narrow circumstances.
But until we know more, I have installed a “maintenance mode” plugin, put the site in maintenance mode with an apologetic message, and deactivated and deleted the s2member and s2member Pro plugins. Not great for our members, but better than getting hacked.
Hi guys.
Yes, I’m aware of that report, and am working on the fix to release it soon.
I won’t give the details here, but it’s something that can happen only under a combination of circumstances, so most aren’t affected by it.
If someone wants me to check his site to tell him if he’d be affected, you can email me at support@wpsharks.com with the site’s address so I take a look.

Thanks Christian!
Thanks Christian and Bill. Good luck
Hi all! Quick update: @clavaque did take a look at my site, and he assured me that this vulnerability would not affect it. Thanks, Cristián!
I did have trouble reaching the email address he gave above; not sure if it was an issue with my email or the wpsharks.com server, but my emails were not delivered.
But if you have a Pro membership and you use that contact form I described above, you should be able to use that form to reach him.
Thanks again, Cristián! I really appreciate the help, and good luck with the fix.
This is a disaster, CVE says they reported it Dec 2 and it still hasn’t been patched?
Is there any response from S2 Member? It’s been at least 11 days since this was announced. I’m a bit surprised my client’s IT hasn’t demanded that S2 Member Pro be removed from all 6 of their sites. I need a response with some indication of when this will be fixed.
The disaster is that the topic was already deleted! If that bug is existing it’s really serious
Looks like they are working on this according to another older thread:
Hello. I didn’t realize this was a duplicate post (original post , though it’s not showing on forum). As per the thread, Cristian is working on it. He suggests contacting him ( support@wpsharks.com) with your site URL so he can verify it’s secure in the meantime before he finds a fix. I will do so.
I’ve sanitized my original post to avoid advertising the issue.
MB
I hid it from the forum listing to make it less obvious for potentially bad actors. You can still find it if you’re in the conversation.
I am receiving an alert that there is a critical vulnerability in S2member (pro).
Here is the link to the original vulnerability report
Is this something you are aware of and will a patch be available?
According to the author there should be a patch soon but no ETA has been given
https://forums.wpsharks.com/t/high-risk-vulnerability-remote-code-execution/12522/10