I can reproduce it all day long but it’s a false start. The 403 Forbidden was generated because of my S3 permissions.
The IAM user I created was given the AdministratorAccess permission but the bucket itself is setup default. So these setting were acceptable to just go to town with file protection. When I move on to setup CloudFront
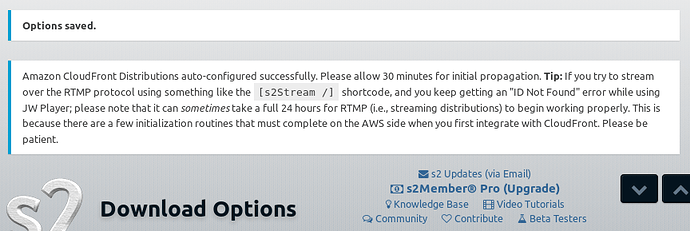
I also receive the message.
Unable to auto-configure Amazon CloudFront Distributions.
Error code: 403. Error Message: Unable to create Amazon CloudFront Origin Access Identity. Unable to create Amazon CloudFront Origin Access Identity. Forbidden
When I google the 403 error I am told that it was the Bucket policy could not be written automatically but when I went to manually create the bucket policy it was a false report. The configuration was there but the API gave me a false positive. All I actually did was wait for CloudFront to finish deploying and everything worked as expected.
So even though s2member displayed an error it was a communication error not a deployment error if that makes sense. I suspect based on my results if I made the bucket public I would not be given the error.
That said it would be wonderful to have much cleaner instructions for the S3 permissions configuration, All documents I could find are old enough that it was not even close to apples to apples and if I reduced the permissions to what I considered the logical minimum but them I just got no love at all.